Protecting Your Business Email: Why Email Authentication Matters
In today's digital business environment, email remains the primary channel for professional communication. However, this critical business tool is...
2 min read
Mark Poulding
05-Jul-2022 17:15:21

We have all received emails that look genuine but turned out to be a spoof or impersonation. Imagine if your clients were to receive an email spoofing your organisation. This is where DKIM and DMARC can be activated to combat impersonating your organisation. In this article, we explain:
Emails that appear genuine, can be fake. They could look like a familiar brand, for example, Microsoft, HM Revenue, or one of your suppliers. They often create a sense of urgency to:
Trick you into revealing sensitive information such as login credentials, credit card details, phone numbers and account numbers.
Click links to a malicious website.
Open an attachment/zip file containing a virus.
Clients see you as a trusted partner and are therefore more likely to follow instructions that you have emailed them, such as new payment details. This is why cybercriminals could attempt to impersonate your organisation - sending emails to your supply chain and client base.
Cybercriminals also target employees by impersonating senior managers. Staff naturally follow instructions from senior managers, even if they seem out of the ordinary.
When a spoof or impersonation email is not prevented by cyber security controls or identified by the recipient, there is a risk of being extorted and damaging your brand reputation.
Yes, without the right controls in place, it is possible that hackers can impersonate you. They can attempt to use your business' domain, or alternatively, use a similar-looking email address/domain or 'false domain', which at a quick glance, can look legit.


In Office 365, with Outlook, DKIM and DMARC can be activated to prevent email spoofing. Activating DKIM and DMARC will identify whether an email is legitimate or a spoof – even if the hacker attempts to copy your domain or intercepts/edits an email directly from your email account.
DKIM and DMARC work together to provide a reliable method to both:
Prevent impersonations
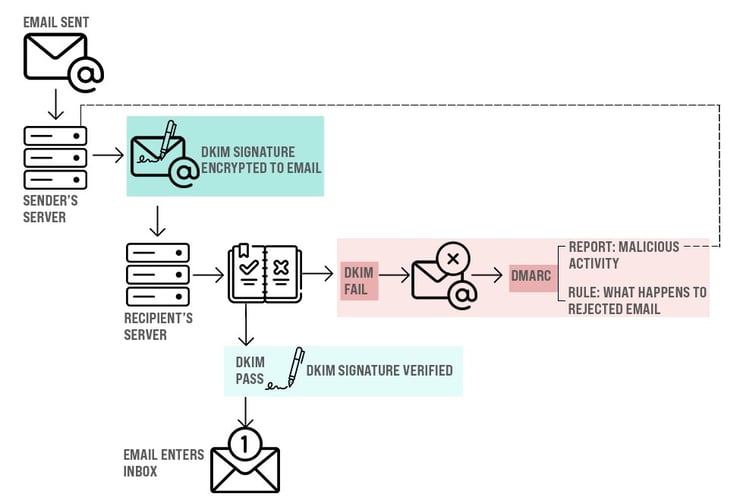
DKIM stands for Domain Keys Identified Mail. It works by checking an email is really from you.
When DKIM is implemented, all sent emails (from the legitimate sender) become encrypted with a signature. The unique DKIM signature is not visible to the sender or receiver - it sits in the background. The receiving servers and email systems can detect the DKIM signature and use it to check it's really you - authenticating the message to ensure:
It is from the organisation/domain it claims to be from
Check the message has not been modified
When the DKIM signature check is complete - if the unique DKIM signature is detected, it passes and enters the recipient's inbox.
DMARC stands for Domain-based Message Authentication, Reporting & Conformance.
DMARC is part of email authentication, working alongside DKIM. A DMARC policy provides a set of instructions of what to do if an email doesn't pass DKIM at the receiving server.
DMARC reports are created using data collected from the servers receiving your emails. These reports can identify possible authentication issues and malicious activity.
Implementing DKIM and DMARC requires technical know-how and can not be achieved by simply 'switching on' like a light switch.
We can help your organisation prevent being impersonated by implementing DKIM and DMARC. There are several stages before DKIM and DMARC is effective; this includes a learning period where emails are first analysed, before the DKIM signature and DMARC are applied.
Book time with our Cyber Consultant to request more information about implementing DKIM and DMARC.
DKIM and DMARC form part of a multi-layered approach to cybersecurity. We help small and medium-sized business implement a proportionate level of security to their business, which is affordable. See our cybersecurity packages for more information about what cyber controls are included.

In today's digital business environment, email remains the primary channel for professional communication. However, this critical business tool is...

Email filtering helps to stop spam and junk mail from entering your inbox. But there will be instances where email filtering systems need your help...
Download our Cyber Security email campaign template! The email templates are designed to raise employees’ awareness of cyber security and highlight...