What is Phishing?
A recent survey reported that 90% of organisations had been subject to a phishing attack. You may have heard of ‘phishing’ but do not know what is...

Let's explore the personal threats and blackmail tactic used in emails by hackers. Understand what blackmail phishing emails look like and what to do if you receive one.
Cybercriminals use many tactics to extort money. This includes bribery. Be wary of blackmail phishing tactics being used by hackers to extort payments, normally using Bitcoin cryptocurrency.
Commonly, hackers will impersonate big brands such as Microsoft, PayPal and Apple or your bank to seem legitimate, other times they may use underhand tactics and personal threats to blackmail you.
So what does a phishing email look like that uses a personal attack? Below is an example:
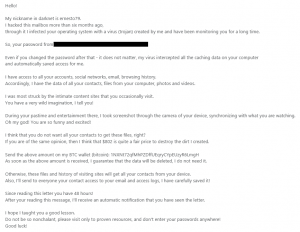
|
Naming your password or old a password |
They have disclosed that they have been monitoring your computer for 6 months and know your password. This is certainly unnerving. Let's remember, you can not be sure at this point whether they have been monitoring your activity. Their primary goal is for you to pay the ransom. How did they get your password? Remember to regularly check whether your email has been hacked. |
|
Monitoring "accounts, social media, email, browsing history" |
While you may use all of these applications, the list is generic and would be relevant to most people. There are no specifics, so this could be a lucky or educated guess based on your demographics. |
|
Belittling and provocative |
'I was most struck by the intimate content sites that you occasionally visit'. Designed to elicit feelings of shock, shame and humiliation, but once again, there are no specifics, with a statement that is vague and realistically, this would potentially be relevant to most people's online activity. |
|
The blackmail |
The screenshot and sending to your contact list. |
|
Bitcoin ransom |
Often used by criminals to hide and launder money because it is not traceable. |
|
48 hours to pay |
They know their sales and marketing! Just like DFS' bank holiday offers or Amazon's Black Friday deals, having a short timeframe creates a feeling of urgency and often a knee-jerk reaction to click on the link (or purchase the latest Amazon gadget, again!) |
Receiving this email is a big worry and action needs to be taken. But it’s important not to panic and make any rash decisions. Go through this list step by step.
It’s always best to get a second pair of eyes on the email to check its legitimacy. An IT support company with cybersecurity expertise will have seen this or something very similar before, so it’s worth speaking to them if you can. Get their advice! They may need to warn other users in your organisation if it has been mass sent.
The first thing you must do is change your passwords. Our guide to creating strong passwords can assist you in this. Change your password from a different device.
If you use the password for more than one website, you must change the password everywhere it is used immediately to something secure. Never use the same password twice and don't use anything that’s easy to guess. We recommend using a password manager such as LastPass and two-factor authorisation where possible.
Don't click on any of the links in the email. This is more than likely, the gateway to access your computer and to do just what they have threatened. The link is more than likely to be malicious.
This isn’t the sort of thing you want to keep in your inbox. Once you have alerted your IT support about the email, you would typically be advised to delete the email from your inbox and block the sender. If you don't have IT support, contact the National Cyber Security Centre for advice.
Easier said than done, however, no matter how big the threat is, don't panic and don't make the payment. Even if you become locked out of your computer, contact the National Cyber Security Centre or your IT support before making any kind of payment.
If you’re looking to make your business cyber safe, remember to lean on an expert and ask lots of questions. Hopefully, we have answered many of your questions about blackmail emails in this article today.
How do your cybersecurity defences stack up? Take a look at our security packages to understand what good cybersecurity looks like for a small business. If you still have questions about your business' cybersecurity, then why not schedule some time with one of our experts.

A recent survey reported that 90% of organisations had been subject to a phishing attack. You may have heard of ‘phishing’ but do not know what is...

Last week, details of FatFaces’ cyber-attack surfaced. Some incredible details were reported from the attack, including screen shots of negotiations...

Accountants deal with thousands of pieces of data every day which makes them a high target industry for cyber crimes. The ever-changing landscape of ...