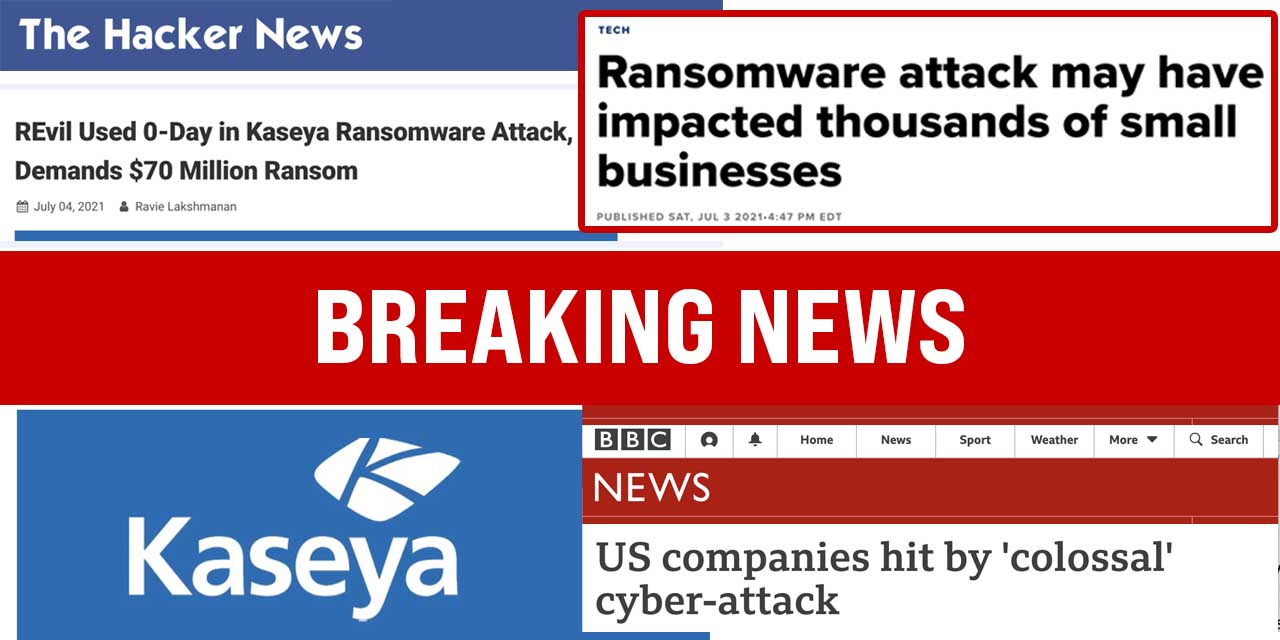
Statement on Kaseya hack affecting small businesses worldwide
You may have seen in the news over the weekend, Kaseya had a massive ransomware attack which has affected thousands of small and medium-sized...

The on-premise Microsoft Exchange Server vulnerability has revitalised the ongoing debate; Cloud vs Traditional IT.
Watch Mark's video summarising what has happened and what it means to your business if you have a on-premise Microsoft Exchange Server.
Businesses with an on-premise Microsoft Exchange Server have been affected by the vulnerability, specifically their Outlook email and calendar. Whereas businesses with cloud based Office 365, have not been affected.
This is an example of where cloud has outperformed traditional IT at keeping data secure. Cloud computing has grown in popularity over the past few years, having a range of benefits. The vulnerability may prove to be the catalyst for moving email and other elements of your business to the cloud.
This article analyses on-premise Microsoft Exchange Server vulnerability, how it affects businesses and what to do next:
On-premise Microsoft Exchange Server vulnerability
Who has been affected?
What programs are affected and what has been stolen?
How could cyber criminals gain access?
How do I find out if I have affected?
What should I do if I have a on-premise Microsoft Exchange Server?
What to do next? What are my options?
On March 2, Microsoft announced that businesses running on-premise Microsoft Exchange Server should urgently update their servers. A zero-day vulnerability had been uncovered. This means an ongoing flaw in the network had gone unnoticed by Microsoft’s developers for some time. Cyber criminals have taken advantage of this flaw and continue to if the security update isn't made.
A Chinese, state-sponsored hacker called ‘Hafnium’ is thought to be behind the attack. The vulnerability has been remained undiscovered for around three months:
Microsoft has detected multiple 0-day exploits being used to attack on-premises versions of Microsoft Exchange Server in limited and targeted attacks. Microsoft Threat Intelligence Center (MSTIC) attributes this campaign with high confidence to HAFNIUM. https://t.co/tdsYGFICML
— Microsoft Security Intelligence (@MsftSecIntel) March 2, 2021
Any business that has 2010, 2013, 2016 and 2019 versions of the on-premise Microsoft Exchange Server are affected. Microsoft Exchange is very popular and primarily used by businesses. Unlike many cyber-attacks, this vulnerability will touch a vast array of organisations: businesses of all sizes -big and small, across multiple sectors. From local government, healthcare and banks through to shops, electricity companies and manufacturers.
It could affect upwards of 250,000 businesses – this is huge!
In essence, hackers can steal the contents of your inbox. Information in your inbox, sent items, drafts and folders can potentially be accessed.
As well as accessing your email, hackers can potentially send emails from your email address to contacts or customers. In addition to this, hackers can potentially access and steal information from your network too - this is information stored within your IT infrastructure.
The hackers have been able to gain access to Microsoft Exchange servers by:
1. Exploiting an unknown vulnerability in the software
2. From there, the cyber-criminal can control the compromised server remotely
3. Data from the organisation’s network can then be stolen
If you are unsure, contact your IT department of IT support service to find out how your emails are hosted.
Microsoft issued security patches for the 2010, 2013, 2016 and 2019 versions of Exchange, however, even after four days following the patch being released, 99,000 servers were still running, and had not been patched.
What’s interesting is the 2010 version is out of service, yet Microsoft took the unusual step to release a security update for that version too – indicating the seriousness of the attack and the sheer number of servers that have been affected. So, make sure your server is updated.
The attack highlights one of the downfalls of running your own servers – more responsibility to maintain security. However, it is important to consider what is best for your business. The cost, implications and security should all be evaluated.
Hosting emails on-site has other downfalls too:
If you have any concerns or questions, then please do not hesitate to get in touch with one of our IT and cyber experts.
You may have seen in the news over the weekend, Kaseya had a massive ransomware attack which has affected thousands of small and medium-sized...

A recent survey reported that 90% of organisations had been subject to a phishing attack. You may have heard of ‘phishing’ but do not know what is...

Last week, details of FatFaces’ cyber-attack surfaced. Some incredible details were reported from the attack, including screen shots of negotiations...