Email blackmail phishing scam
Let's explore the personal threats and blackmail tactic used in emails by hackers. Understand what blackmail phishing emails look like and what to do...

A recent survey reported that 90% of organisations had been subject to a phishing attack. You may have heard of ‘phishing’ but do not know what is it? By the end of this article, you will understand what phishing is, what they look like and how to spot a phishing scam.
In short, phishing is a type of cyberattack that tricks people into:
Clicking on a malicious link
Disclosing confidential information
Transferring money
Any form of communication, including, text, email, letter and telephone. Scammers will use whatever channel works, so the list goes on and it will continue to adapt.
Phishing attacks are usually under the guise of reputable, trustworthy, household brands; Microsoft, Amazon, WhatsApp, Facebook, Outlook, Apple, Paypal, Netflix recently topped the most impersonated brands in phishing attacks. Coronavirus-related phishing attacks have also been prevalent recently.
Scammers imitate trustworthy brands or government agencies because you are more likely to trust and follow their instructions. Combine this 'authority' with a message that creates urgency or emotion such as panic (payment failed), elation (register to claim tax back) or may satisfy your desires or if something is in short supply (fast track for coronavirus test/vaccine), and you can see how it is very easy to have a knee-jerk reaction and click on that dodgy link!
Aside from famous, everyday brands, you may be receive phishing scams from someone you know or a local business that you have been in contact with. When an individual is hacked, a hacker could send phishing scams to all contacts in their address book in the guise of the victim. If you receive a random email or Facebook message from a friend or relative asking to transfer money, definitely speak to them directly to double-check the authenticity!
Many businesses fall victim to cyber-attacks or data breaches. Similar to an individual attack, a malicious email or message can be addressed from a business that you know.
On a base level, there are two different types of phishing attacks; un-targeted and targeted (spear).
An un-targeted phishing attack will cast out some ‘bait’ to a large number of people. The cyber attacker's aim is to get anybody to click a malicious link that has usually been delivered by email.
As the title suggests, the attackers will not target a particular person or business. As the attack targets anybody, it makes the attacks quick to create and execute. The contents of phishing attacks change on a regular basis due to them having a short life before they get compromised and blocked. The majority of the time they are easy to spot and have a low success rate. Some may feel personal attacks and could even incorporate blackmail, but have been mass sent.
As you have probably guessed already ‘targeted (spear) phishing’ is an attack that will target a particular user or business. These attacks can take months to plan and execute as they take extensive research. The carefully thought-out attacks will be highly personalised.
Imagine two people are fishing at a pool. A fisherman (untargeted phishing) will be trying to catch a fish in the pool. Meanwhile, a spear-fisher (targeted phishing) will be trying to catch a specific fish.
If you regularly use email, there’s a high chance you have received a phishing scam. Below are some real-life examples of phishing attacks.
The classic phishing email is being told you’ve won a too good to be true prize or amount of money? That’s because it is too good to be true. They are fake, they just want your bank account details and should be deleted as soon as you get them. Another method of getting bank details is by alerting people to a missed payment or problem with an online account. Often these E-mails will look like they’re coming from a bank or mobile phone provider telling the user they need to log in with their details. These E-mails will contain malicious links that should not be clicked under any circumstance.
Some phishing scams are more obvious to spot than others. If you receive an email telling you have won an extortionate amount of money from an offshore bank account, it’s going to be fake. But what should you look for if the scams are more sophisticated and complex?
This is one of the main giveaways when it comes to phishing attacks. Would a multi-million-pound professional company really send an email littered with spelling and grammatical errors? We are a nation of skim readers and often miss even the most basic errors. If an email seems important, always double-check the authenticity.
As you can see with the above example the email, there are numerous grammatical errors:
Always be wary of unknown email addresses. Phishing attacks will usually be sent from rogue email addresses. Take a look at the example below:
But do be careful, hackers are getting ever more sophisticated. The image below is an email, spoofing Microsoft Outlook. It uses the exact domain, and was recently used in a spearing attack to attain victim's Microsoft 365 login details/credentials.
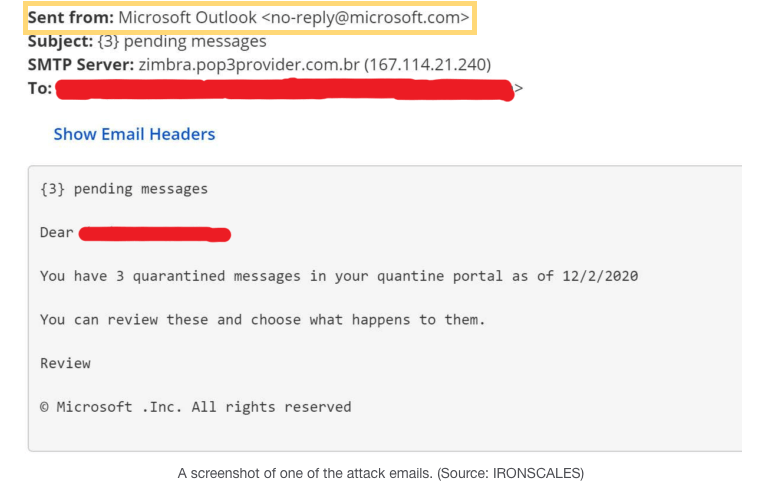
The majority of phishing scams direct you to click on a link. Simply clicking on a link can be enough to cause damage. Your computer can be unknowingly infected with malware. Malware can log your movements and essentially steal your data.
This can easily be prevented though. If you hover over a link within an email, the address that you would be set to (if you were to click) can be previewed. Before proceeding to click, always view the address. Quite often it's very evident that you are being taken to a very different URL to what is advertised.
Ideally, you should never click a link within an email - it's best practice to contact the business directly. Search for the company directly in Google and contact them using their direct contact details. Always question links in emails, especially when you are not expecting them.
If you’re looking to make your business cyber safe, remember to lean on an expert and ask lots of questions. Hopefully, we have answered many of your questions about phishing in this article today.
If you still have questions about your business' cybersecurity, then why not schedule some time with one of our experts.
If you want to keep up to date with the latest cybersecurity tips, then subscribe to our newsletter.
Learn about our cybersecurity business packages and pricing to understand what coverage your small or medium-sized business might need.

Let's explore the personal threats and blackmail tactic used in emails by hackers. Understand what blackmail phishing emails look like and what to do...

Accountants deal with thousands of pieces of data every day which makes them a high target industry for cyber crimes. The ever-changing landscape of ...
What is cybersecurity awareness training? Cybersecurity awareness training is the formal education of business security to non-technical employees....