Urgent WordPress plugin update and more IT & cyber news
Urgent WordPress plugin updates, broadcaster down-time and real cyber-attack negotiations, here is my weekly round-up of mainly cyber news this week:
6 min read
James Cash 01-Apr-2021 17:05:31

Last week, details of FatFaces’ cyber-attack surfaced. Some incredible details were reported from the attack, including screen shots of negotiations with the Canti cyber gang.
I closely follow the cyber news and this type of detail is rarely revealed. This is why these intimate details are so significant. Later in this article are screen shots of the negotiations between FatFaces’ negotiators and the cyber-gang. Quite astonishingly the cyber-criminal also advise how to prevent a cyber-attack in the future. In the article we will cover:
Cyber attack Taboo = under-reported cyber crime
How is this relevant to businesses in the West Midlands?
What negotiations between a cyber gang and victim look like
Sequence of events of a ransomware attack
What security would a cyber-criminal recommend?
What should Birmingham businesses do next?
What if I have been victim of FatFace’s cyber-attack?
What should I do if my business has been victim to a cyber attack?
Cyber-attacks remain under cloak and dagger. The Cabinet Office's 'The cost of Cyber Crime' report suggests there is a "lack of available data and what we believe to be a significant under-reporting of cyber crime."
Cyber attacks are taboo: reputational damage and the fear of losing trust with customers and suppliers are the main reasons why many businesses keep it to themselves.
In reality, most businesses will have had some kind of cyber attack attempt. It is reported that last year alone, UK businesses had 20% rise in cyber attack attempts compared to the previous year, facing an average 686,961 attempts to breach their systems online.
Of the cyber crimes reported, figures are notably rising. Most recent figures from the Department for Digital, Culture, Media and Sport's 'Cyber Security Breaches 2021' report suggests that 27% of businesses and 23% of charities experience some form of a cyber attack at least once a week. The most common by far are phishing attacks (83% businesses, 79% charities). This is followed by impersonation (27% businesses, 23% charities).
Let’s remember that cyber-criminals are indiscriminate. Any business can be targeted, no matter their size. Cyber attackers are not interested in what you do, they are interested in extorting money. Cyber gangs are based around the world - it really doesn't matter to them where you are based, you are still a target.
The insights and lessons that can be learnt from this attack can be applied to any business - across all sectors and all business sizes. So if you are a small or medium business based locally in Dudley, Stourbridge, Worcester, Wolverhampton or Birmingham – here are what negotiations with a cyber-criminal look like:

Computer Weekly have reported the following sequence of events took place for FatFace:
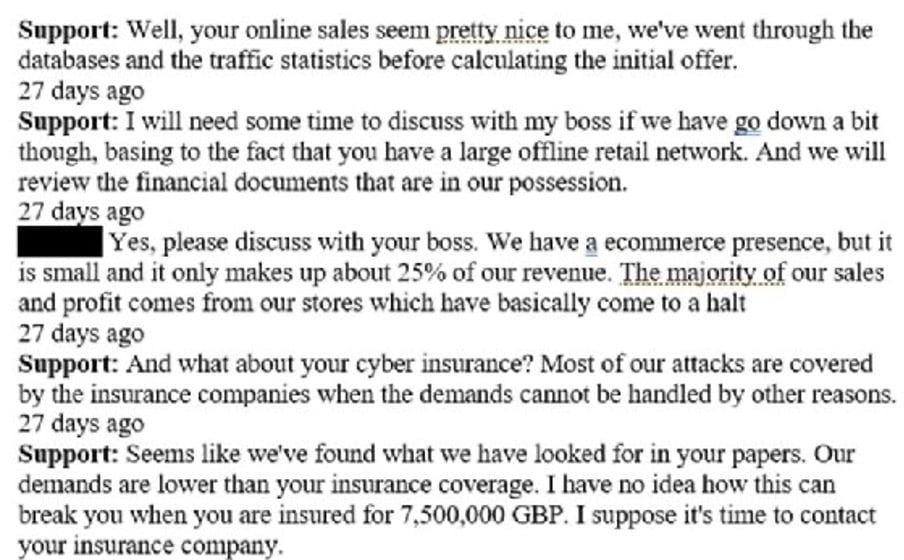
|
Support: Well, your online sales seem pretty nice to me, we've went through the databases and the traffic statistics before calculating the initial offer Support: I will need some time to discuss with my boss if we have go down a bit though, basing to the fact that you have a large offline retail network. And we will review the financial documents that are in our possession. Negotiator: Yes, please discuss wit your boss. We have a e-commerce presence, but it is small and it only makes up about 25% of our revenue. The majority of our sales and profit comes from our stores which have basically come to a halt. Support: And what about your cyber insurance? Most of our attacks are now covered by the insurance companies when the demands cannot be handled by other reasons. |
|
Support: We are ready to make it fast, but we need a better offer. Make a step towards us and we will make the same. Let's make it faster by walking towards each other in a more timely manner. Support: Give me half an hour. We will discuss on how to make it faster and I will get back to you Negotiator: Okay I will be here. Of course, the lower the price, the fast it ca be for us to approve. I will wait to hear from you. Support: We have had an urgent meeting. I could convince everyone that we want this deal to be closed by the end of the week and managed to get you a new price that is way way better than the previous one. We are ready to accept $2.65mil Negotiator: Thank you very much for this. I will tell everyone immediately and we will have a meeting tomorrow to discuss. We would also like this to be closed. |
Here are the security measures recommended by Conti gang to FatFace following their cyber-attack:
Check what security measures you already have in place. Ask your IT department to list what you currently do. If you have outsourced IT support, look at your invoice and work out what security coverage you currently have. If your IT support has not offered you these fundamental best practice security measures, I would also question whether they take cybersecurity seriously and if they have your best interests at heart.
Cybersecurity has evolved and outsourced IT providers should be proactive. The best IT support businesses will communicate security measures they recommend for your individual. Cybersecurity measures are affordable to SMEs today, but ensure your IT department has time to implement and report on your security. If they spend their time firefighting issues todays (e.g. printer not working), then they will not have time to consider tomorrows threats.
We offer the Enhanced Security Package to our clients. This contains all of the cyber-criminals recommended cybersecurity measures and more, for example, ongoing staff training. If you remember, the attack likely began because an employee clicking on a spam link within an email (phishing attack). Being able to spot and report spam links could prevent an attack from ever taking place.
FatFace have already notified customers that some personal data, including names, postal and email addresses and limited credit card data, have been compromised. They are also offering affected customers a 12-month subscription to Experian’s identity theft service. We would highly recommend taking them up on this offer if you have been victim to the attack.
If you need help creating a cyber response plan or cybersecurity, get in touch or request a call back.

Urgent WordPress plugin updates, broadcaster down-time and real cyber-attack negotiations, here is my weekly round-up of mainly cyber news this week:

Understanding the risks of cyber threats to your business, enables you to it place the right level of cybersecurity controls to your business. Even...

Let's explore the personal threats and blackmail tactic used in emails by hackers. Understand what blackmail phishing emails look like and what to do...