3 min read
Is your IT support company genuinely proactive?
If you have ever been in the position of looking for a new IT support company, you will know what I mean when I say it is hard to tell IT companies...

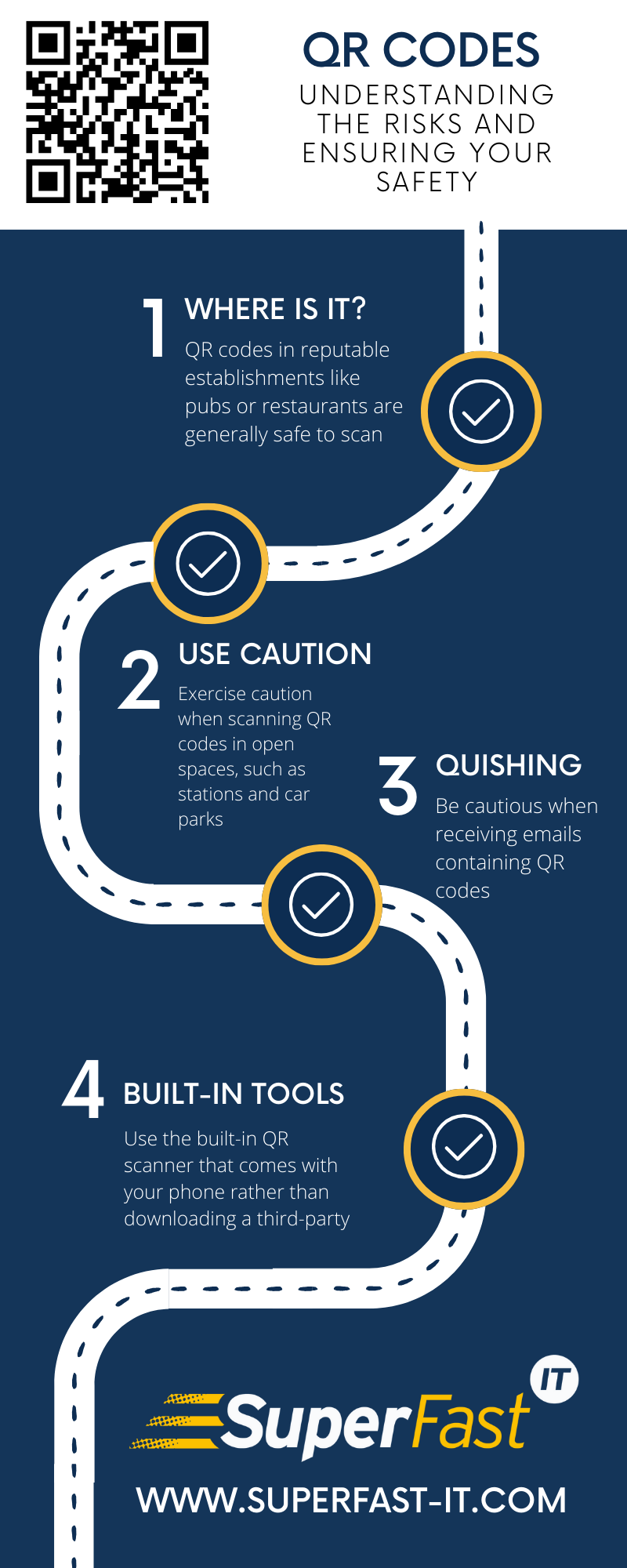
QR codes have become ubiquitous in our daily lives, especially since the COVID-19 pandemic. They are used for various purposes, such as ordering food, logging into devices, and making payments.
While QR codes offer convenience, it is crucial to understand the potential risks associated with scanning them.
According to a report by BBC News, there have been increasing instances of QR code-related fraud in the UK.
================================
Grade your organisational risk with our comprehensive cybersecurity quiz.
🎯 Grade Your Organisational Risk: CLICK HERE
================================
These scams often occur in public spaces like stations and car parks, where criminals place malicious QR codes to steal money or personal information. However, it is important to note that QR code fraud is relatively small compared to other types of cyber fraud.
One growing concern is the use of QR codes in phishing emails, a technique known as "quishing." Criminals are increasingly using QR codes to disguise links to malicious websites, as people have become more cautious about clicking on suspicious links in emails.
Additionally, some security tools designed to detect phishing emails may not scan images, allowing QR codes directing users to malicious websites to slip through undetected.
When scanning QR codes, users are more likely to use their personal phones, which may not have the same level of security protection as employer-provided computers.
This makes personal devices more vulnerable to potential threats.
To protect yourself from QR code-related risks, consider the following:
By staying informed and taking appropriate precautions, you can safely navigate the world of QR codes and enjoy the convenience they offer without compromising your security.
Grade your organisational risk with our comprehensive cybersecurity quiz.
🎯 Grade Your Organisational Risk: CLICK HERE
================================
Our quiz is more than just a set of questions; it's a window into your organisation's cybersecurity posture. By participating, you're not just testing your knowledge; you're evaluating your organisation's readiness against cyber threats.
As your trusted MSP, we're committed to helping you navigate the complex world of cybersecurity. This quiz is the first step in a journey towards a more secure digital environment for your business.
Take the Quiz Now and pave the way for a safer digital future for your organisation. Remember, in the realm of cybersecurity, knowledge is not just power – it's protection.

3 min read
If you have ever been in the position of looking for a new IT support company, you will know what I mean when I say it is hard to tell IT companies...
4 min read
A slow internet connection can seriously disrupt your day — whether you’re working remotely, running a business, gaming, or just trying to stream...

2 min read
Selling, donating or recycling laptops and other devices Whether you are looking to donate, sell or recycle an old computer, laptop, tablet or phone,...