2 min read
25 most common passwords
‘Please create a secure password’. How many times a year do you read this and think I’ll stick to the password I use for every other site, and it...
4 min read
Editor 19-Apr-2024 16:19:22

*(Hand image courtesy of ncsc.gov.uk)
Nearly five years after the original publication, "Three random words” or #thinkrandom is still one of the most visited pages of the NCSC website. It tells you how, with the help of three random words, you can make a password 'random enough' to keep the baddies out but simultaneously 'easy enough' for you to remember.
================================
Grade your organisational risk with our comprehensive cybersecurity quiz.
🎯 Grade Your Organisational Risk: CLICK HERE
================================
We pretty much all recognize at this point that forcing complexity requirements is are bad defence against guessing attacks. We find it hard to remember random character strings, and so our mind makes up predictable patterns (such as replacing 'o' with zero) so that they make up the required 'complexity' criteria. Adversaries know such tactics and can use such information to generate optimised attacks. The application of such complexity requirements makes the creation of passwords more predictable.
Faced with creating yet another password with a bunch of specific requirements, users usually resort to some variation of a hack for something they already know and use, fooling themselves that it's strong since it passes the password strength metres (and is accepted by the online service).
None of this is helped by long-held, terrible advice, where passwords must be memorised and, in no way, shape, or form, can be stored (whether in a password manager, in your browser, on paper) without it risking your security.
The other concern is the continued low uptake of password managers to store and generates passwords (the NCSC has been encouraging organisations and individuals to use password managers for some time now).
To be absolutely clear, the National Cyber Security Centre (NCSC) states, “There are a number of ways you can securely store your passwords, in a password manager, a browser, or on a piece of paper, so remembering them is no longer a problem.”
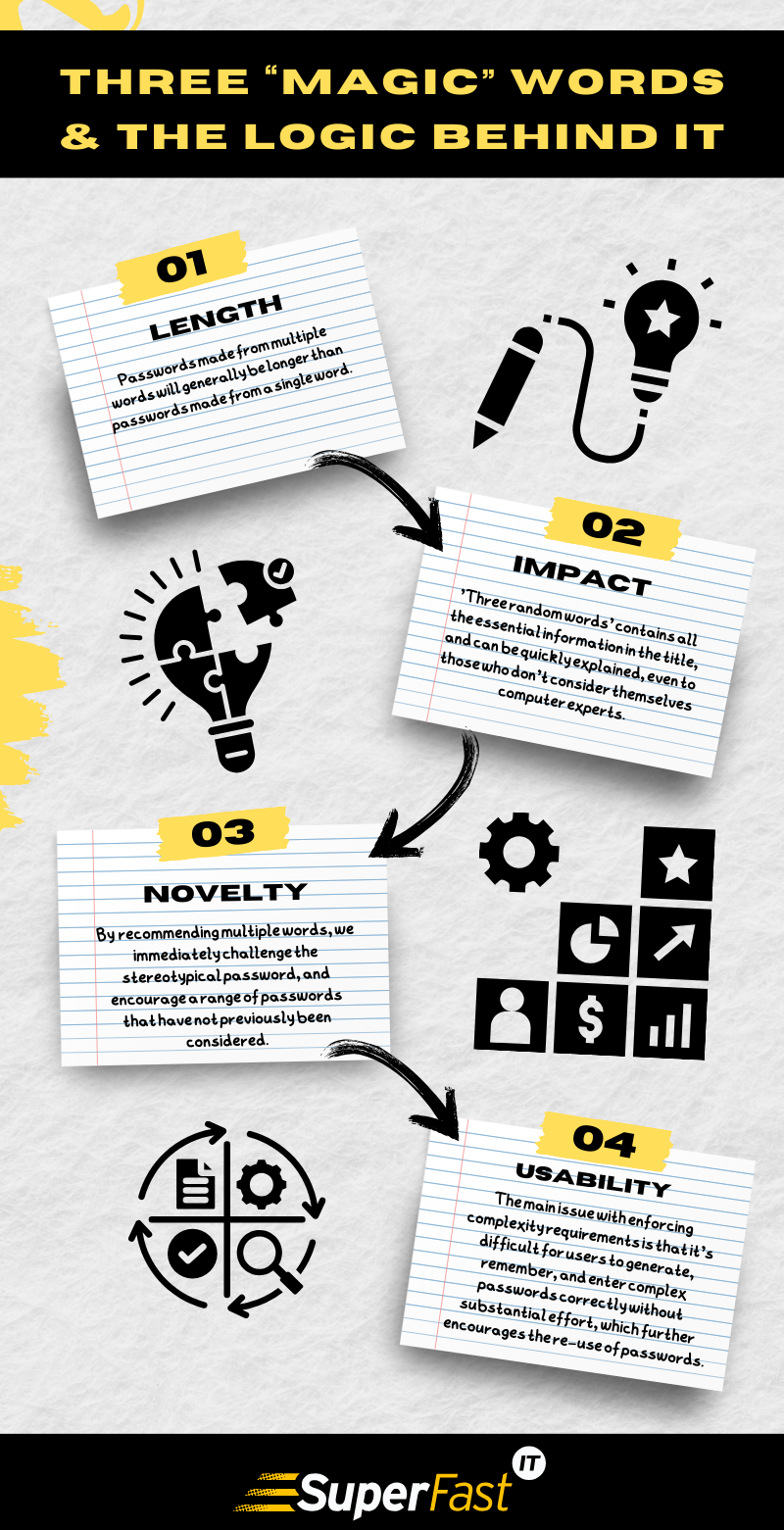
Passwords are the first line of defence in cyber security. The 'three random words' method offers a balance between complexity for security and simplicity for user recollection.
The strength of a password often hinges upon its unpredictability and length. Three random words generate a password that is not only long enough to thwart brute force attacks but also complex enough to resist common guessing techniques. Users can further enhance security by mixing in numbers and capital letters, effectively tricking password strength metres that evaluate the robustness of a password.
Cyber criminals commonly deploy guessing attacks, leveraging data about individuals to crack passwords. A sequence of three unrelated words significantly diminishes the success of such attacks. Each additional word exponentially increases the number of possible combinations, making the password more resilient against both automated and targeted guessing attempts.
Hackers are deterred by the time and effort required to infiltrate accounts with strong passwords. Using three random words creates a password that is challenging to decipher, increasing the cost and reducing the efficiency of cyber criminals' attacks. Consequently, they might opt to bypass these accounts in favour of targets with weaker security measures, thereby improving the overall safety of data.
At home, individuals are encouraged to adopt the three-word formula for its simplicity and effectiveness. In the workplace, this strategy harmonises security protocols cross-government and in the private sector, making passwords memorable to the user yet challenging for cyber attackers. Organisations find this method aids compliance without compromising operational efficiency.
Those who've embraced the NCSC's advice generally report positive outcomes. They find that blending three unrelated words produces passwords that are easier to recall than complex alphanumeric alternatives. Password managers play a supportive role here, securely storing these unique combinations and reducing the mental load of memorising multiple passwords.
Creating a strong, memorable password is crucial for securing one's online presence. This approach balances ease of recall with sufficient complexity to deter unauthorised access.
Usability is crucial in password creation, as password strength is redundant if the user cannot recall it. The NCSC promotes the use of three random words because it offers a password that is both secure against various online threats and is easier for individuals to remember. Instead of impossible-to-memorise string of characters, the combination of words – such as "FalconBridgeButter" – enhances password strength without sacrificing usability.
Password Logic Versus Passphrase:
By sticking to these guidelines, one can craft a passphrase that not only meets security standards but also reduces the brainpower required to remember complex password combinations.
Grade your organisational risk with our comprehensive cybersecurity quiz.
🎯 Grade Your Organisational Risk: CLICK HERE
================================
Our quiz is more than just a set of questions; it's a window into your organisation's cybersecurity posture. By participating, you're not just testing your knowledge; you're evaluating your organisation's readiness against cyber threats.
As your trusted MSP, we're committed to helping you navigate the complex world of cybersecurity. This quiz is the first step in a journey towards a more secure digital environment for your business.
Take the Quiz Now and pave the way for a safer digital future for your organisation. Remember, in the realm of cybersecurity, knowledge is not just power – it's protection.

2 min read
‘Please create a secure password’. How many times a year do you read this and think I’ll stick to the password I use for every other site, and it...

1 min read
Uppercase letters, numbers, symbols and more. Creating the perfect password and remembering it can seem an impossible task. If you’re having trouble...

3 min read
*(based on the NCSC report: Cyber Essentials: Requirements for IT infrastructure v3.1) In an era where digital threats are evolving at an...